With compromised keys, malicious actors can easily bypass important security measures, gaining access to your sensitive data and potentially causing significant damage. What went wrong, and how do you avoid cases like this? Before you face this level of incident, you should take robust security measures, including the most significant ones, in the following paragraphs.
In this article, we’ve got an expert risk management plan specifically tailored for QA leads like you. We’ll guide you through the process and help you avoid potential security breaches.
What is risk management?
When it comes to the risk management definition, we can say it is the process of identifying, assessing, and controlling potential risks that could affect an organisation’s operations or objectives. It involves analysing potential threats, identifying the potential impact of vulnerabilities, and implementing strategies to eliminate or mitigate them.
Regarding QA (Quality Assurance), risk management involves identifying and addressing risks related to software development and testing. These risks could be related to code quality, functionality, security, and performance.
When to use the RBT approach?
As a QA lead, you should apply the Risk-Based Testing (RBT) approach if you aim to enhance the effectiveness of your security plan significantly. RBT involves identifying, prioritising, and managing risks related to software development and testing. Here are some scenarios to use this approach:
- Complex and critical systems: When dealing with complex software systems or critical modules, the RBT approach can be particularly beneficial. These systems often have a higher risk profile, and a risk-based testing strategy helps you tackle potential vulnerabilities and threats.
- Limited resources: If you have resource constraints, the RBT approach can help optimise your efforts by focusing on the most critical areas of your application. With a thorough risk assessment, you can allocate your limited resources to preventing security threats more efficiently and effectively.
- Changing requirements: Rapidly evolving requirements, whether dictated by the market or unforeseen shifts, is another reason to apply the RBT approach to adapt your testing efforts accordingly. You can prioritise testing activities by continuously assessing and reassessing risks and their importance.
- Compliance and regulatory requirements: Companies in regulated industries, such as healthcare or finance, always face strict compliance requirements. The RBT approach can help you meet these requirements by providing a systematic way to identify and mitigate risks that could lead to non-compliance and/or a resulting costly breach.
- Cost-effective testing: Focusing your testing efforts on areas that pose the highest risks will help optimise the use of your resources, making testing more cost-effective while still providing adequate coverage for critical areas.
- Prioritising security testing: If security is a primary concern for you, the RBT approach can help you prioritise security testing activities by identifying and addressing the most significant security risks early in the development lifecycle.
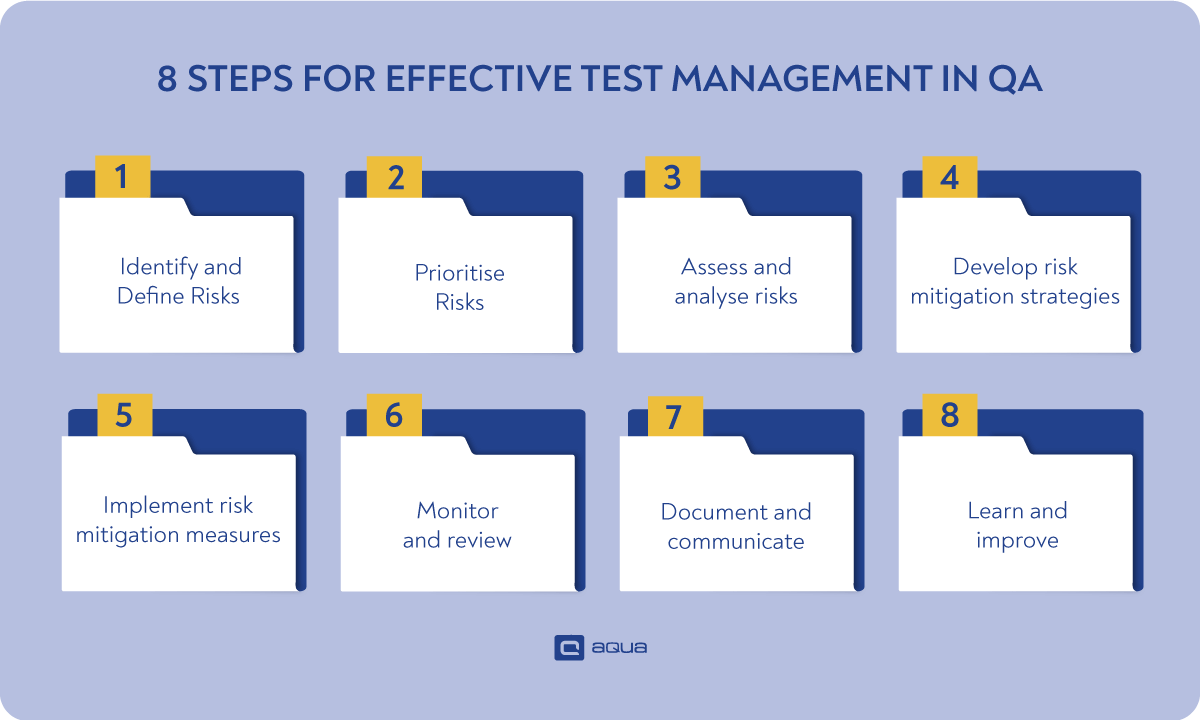
Steps for effective risk management in QA teams
Here are the steps in the risk management process that you should take to proactively address potential risks and thus contribute to the overall success of software projects.
#1. Identify and Define Risks
The first step in effective risk management strategies is identifying and defining the risks in the software development and testing processes. You must engage with stakeholders, QA team members, developers, and other relevant parties to gather insights and perspectives on potential risks and document each one along with its description, potential impact, and the likelihood of occurrence.
It is also highly beneficial to explore what peers in similar companies are saying and to gather user insights based on their poor experiences with competitors. Engaging with peers in your competitors provides an opportunity for knowledge sharing and learning from their experiences. By exchanging ideas and experiences, you can gain valuable insights into risks that may not have been initially identified.
Colleagues can offer unique perspectives on potential risks, share lessons learned, and suggest effective risk mitigation strategies. This collaborative approach helps in broadening the understanding of risks and refining risk management strategies.
Similarly, users who complain about their negative experiences with competitors can offer valuable insights into potential risks and pitfalls to avoid. Their firsthand experiences can shed light on where software products often fall short, enabling you to address such risks in your development and testing processes proactively. Users’ feedback can provide ideas for risk identification that may not have been evident from internal perspectives alone.
#2. Prioritise Risks
After identifying the risks, you should prioritise them based on their potential impact and likelihood. In this step, factors such as the criticalness of the system or application, regulatory requirements, customer impact, and business objectives are critical. This lets you focus your resources on addressing the most significant risks first.
These are the criteria you should consider when prioritising your risks:
- Potential impact on critical system functionality
- Regulatory compliance requirements and legal implications
- Customer and end-user impact
- Business objectives and strategic priorities
- The severity of potential financial losses or reputational damage
- Likelihood of occurrence or frequency of the risk
- Time and effort required for risk mitigation
- Availability of resources and expertise for addressing the risk
- Level of risk tolerance and appetite within the company
"Cybersecurity is not about perfection; it is about risk management."
#3. Assess and analyse risks
What you should do after identifying and prioritising risks is to sit down and perform a comprehensive risk assessment and analysis for each one of them. You should evaluate the likelihood of occurrence, the potential impact on the project, and the ability to detect and mitigate the risk. Using risk assessment techniques such as qualitative and quantitative analysis, risk matrices, and probability and impact assessments will help you understand each risk better.
#4. Develop risk mitigation strategies
Once you assess the risks, you will need appropriate risk mitigation strategies. This includes specific actions to reduce the probability or impact of risks, avoid risks altogether, transfer risks to external parties, or accept them if their impact is deemed acceptable. You should also decide what steps can be automated and choose risk management software to eliminate the manual effort in these steps. Other than that, collaborating with relevant stakeholders is important to determine the most effective strategies for each risk.
An AI-powered Test Management System like aqua cloud can significantly streamline the risk management process for QA teams.
aqua enhances risk prioritisation by providing real-time analytics, and KPI alerts, allowing you to focus on high-impact risks based on their severity and likelihood. With detailed reporting, you gain clarity on potential vulnerabilities, being able to make better-informed decisions. aqua cloud’s integration capabilities with solutions like Jira, Azure DevOps, Ranorex, and many more allow seamless collaboration among stakeholders, ensuring everyone is involved in developing effective risk mitigation strategies. 1-click bug recording integration with Capture will deliver the ability to quickly document and address defects, reducing the risk of unresolved issues impacting your project’s timeline and quality.
Supercharge 100% of your risk management efforts
#5. Implement risk mitigation measures
Now you have to put the risk mitigation strategies into action. This includes communicating and assigning responsibilities to the QA team members and other stakeholders. You should monitor the progress of each mitigation measure and ensure they are effectively implemented within the planned timelines.
#6. Monitor and review
Continuously monitoring and reviewing the effectiveness of the risk mitigation actions comes next. You should regularly assess the status of risks, evaluate the success of your strategies, and track potential new risks that may arise during the testing process. Do not forget to review the risk management plan periodically to ensure it remains aligned with changing requirements, evolving risks, and regulatory compliance.
#7. Document and communicate
Documentation is one of the most significant risk management techniques. You must document all aspects of the risk management process, including identified risks, risk assessments, mitigation strategies, and their implementation status. This includes maintaining a central repository or documentation system where all information is easily accessible to the QA team and other relevant stakeholders. You should communicate risk-related information, progress, and updates regularly for transparency and foster collaboration.
#8. Learn and improve
Risk management is an iterative process, so you have to take note of every single mistake you make during your plans and strategies. The previous step will greatly help you with it because, with good documentation, you will be able to analyse your past projects and develop new risk management solutions for upcoming projects.
Why is risk management important in QA teams?
Risk management plays a crucial role in the success of QA teams and the overall quality of software applications. You can deliver reliable, secure, high-quality software by effectively identifying, assessing, and mitigating risks. Here are some reasons why risk management is crucial in QA teams and its benefits to the software development process.
- Minimising impact: Risk management allows you to identify potential risks early on and take effective measures to minimise their impact. Addressing risks before they become huge can prevent costly rework, downtime, and customer dissatisfaction.
- Better product quality: Effective cybersecurity risk management means identifying and addressing vulnerabilities and weaknesses in software applications. Thorough risk assessments and appropriate mitigation strategies can improve the software’s overall perceived quality and objective reliability.
- Reliable software with no security issues: Security risk management allows you to identify and assess potential security risks, such as data breaches or unauthorised access, and implement robust measures to protect sensitive information and ensure the integrity of the software.
- Resource optimisation: Risk management also helps you allocate resources effectively by prioritising risks based on their potential impact. This way, you can focus your efforts and resources on the most critical areas, optimising testing efforts and ensuring comprehensive coverage where it matters the most.
Common risks in software testing
Here are some security risks you should consider in software testing:
- Vulnerabilities in software: Software applications may contain security vulnerabilities that malicious actors can exploit. Testing should identify and address them, including injection attacks, cross-site scripting (XSS), or insecure authentication and authorisation mechanisms.
- Inadequate authentication and access controls: Insufficient authentication and access controls can lead to unauthorised access to sensitive data or functionalities, so testing should verify that proper authentication mechanisms are in place and that access controls are enforced effectively.
- Data privacy and confidentiality risks: Testing should specifically consider data privacy and confidentiality risks. This includes proper handling and protection of personally identifiable information (PII) or sensitive data stored by the software.
- Integration and interoperability issues: Integration with external systems or components can introduce risks related to compatibility, data exchange, or communication. Testing should validate that the seamless integration and interoperability of the software with ] external systems does not come at the cost of security.
- Performance and scalability risks: Testing should also address performance and scalability risks by identifying potential bottlenecks, testing under realistic scenarios, and ensuring the software can handle the expected user load without performance degradation. It is crucial to address both existing performance risks and anticipate potential risks when scaling up the software to accommodate larger user volumes or increased system complexity. By thoroughly evaluating performance-related flaws and deficiencies, you can proactively identify and mitigate risks, ensuring optimal software performance in current and future scenarios.
- API security risks: If the software exposes its API to third parties, there are extra risks such as insecure API endpoints, inadequate authentication or authorisation mechanisms. It can get as bad as having vulnerabilities in the actual data exchange.
For example, a social media platform might expose APIs that allow third-party developers to integrate their applications with the platform, enabling functionalities such as posting content, retrieving user data, or interacting with the platform’s features. Failing to protect your API adequately can lead to a Cambridge Analytica level of blowback to your reputation and financials. That is why testing should focus on validating the security of APIs and ensuring proper access controls.
Conclusion
By proactively identifying, assessing, and mitigating key risks, you can enhance the overall reliability and security of your products. Addressing vulnerabilities, ensuring proper authentication and access controls, validating data privacy, and addressing integration and performance risks are just a few examples of how risk management contributes to generally better software. As for the security side of things, mitigating these risks through improved workflows will reduce the likelihood of security breaches, protecting sensitive data and shielding you against financial loss.
Ready to go beyond risk management and supercharge all your QA efforts? Discover the power of aqua cloud, the all-in-one AI-powered test management solution that optimises your entire testing lifecycle. With aqua cloud’s AI Copilot, you’ll effortlessly minimise manual work and accelerate test case, test data, and requirements generation processes, 97% faster and with 3 clicks. Experience 100% traceability and visibility into your testing progress, ensuring you stay ahead of potential risks. Our 1-click bug recording integration with Capture makes swift documentation of defects a breeze. Embrace the unmatched precision and unlock a solution that goes far beyond just risk management, taking away the pain of testing.
Maximise the risk management strategy efforts of your QA team with aqua AI







